Continuous Threat Modeling
Build actionable, consistent threat models in minutes, not days. Automatically update threat models with every code change.
Sign up today.Start threat modeling in minutes.
Use Threat Modeling
to Scale AppSec
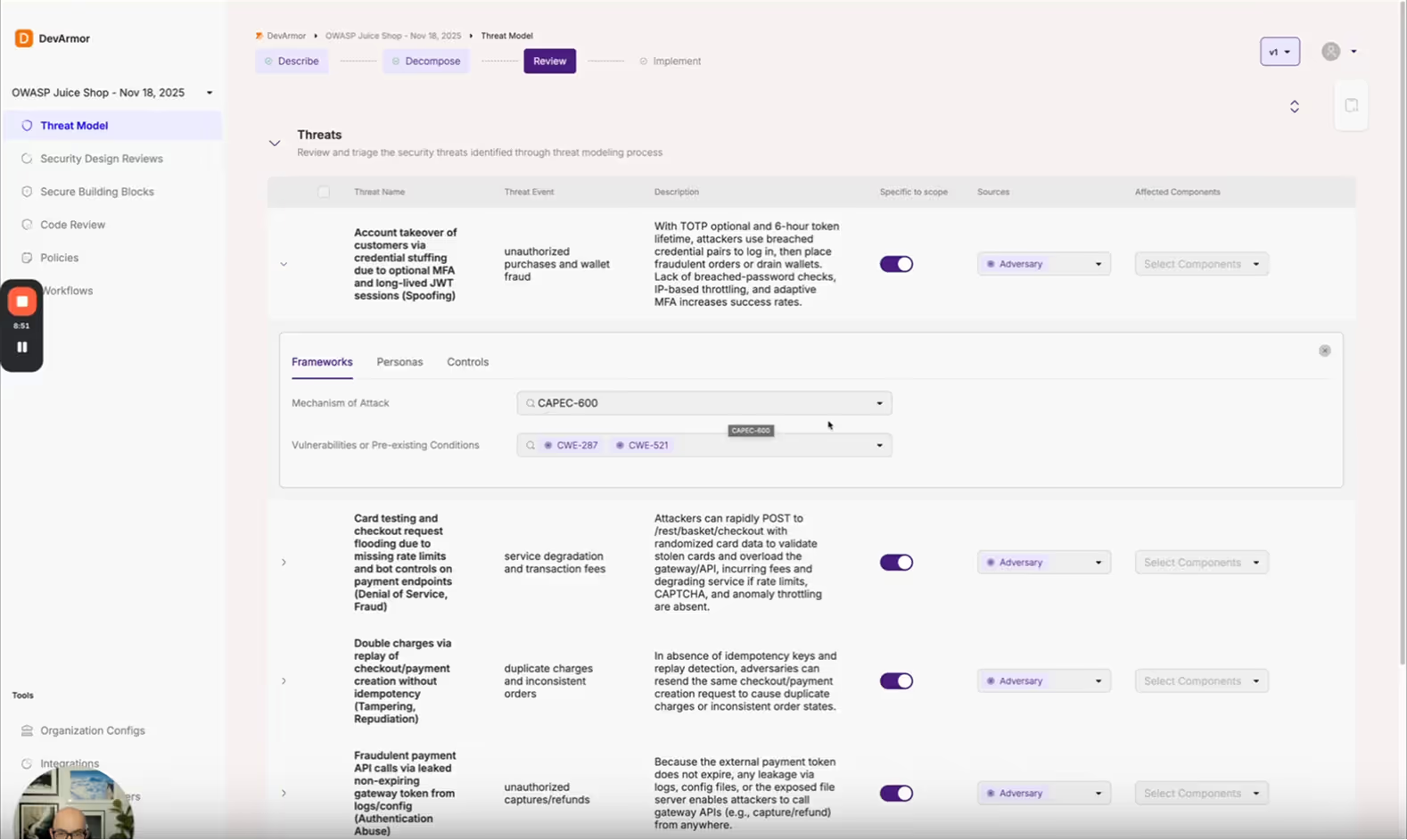
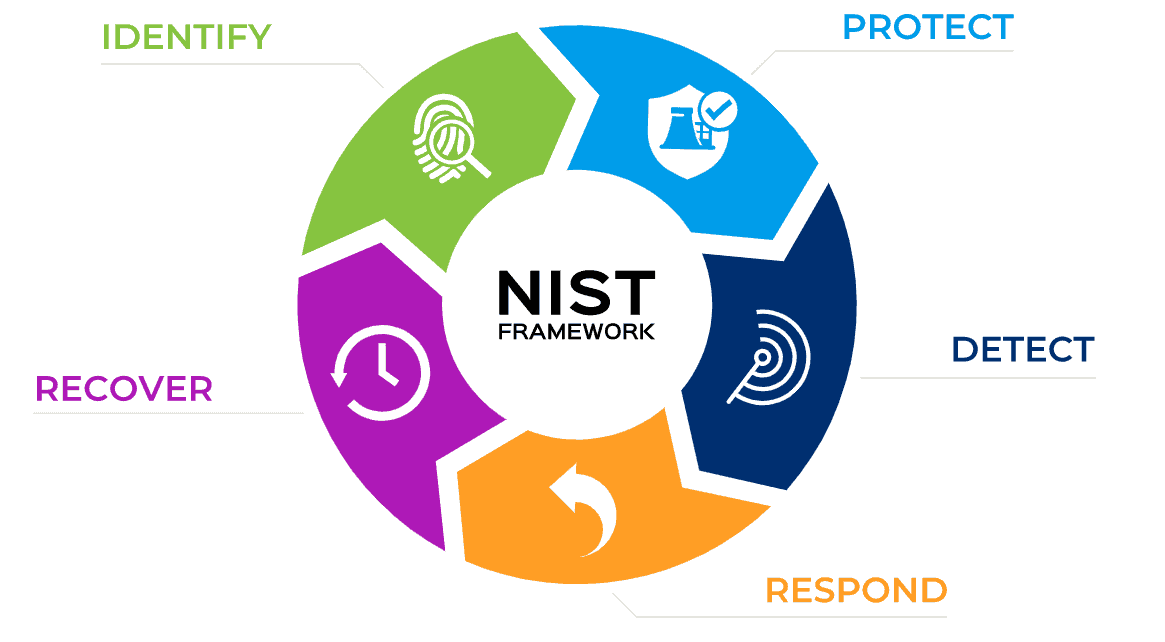
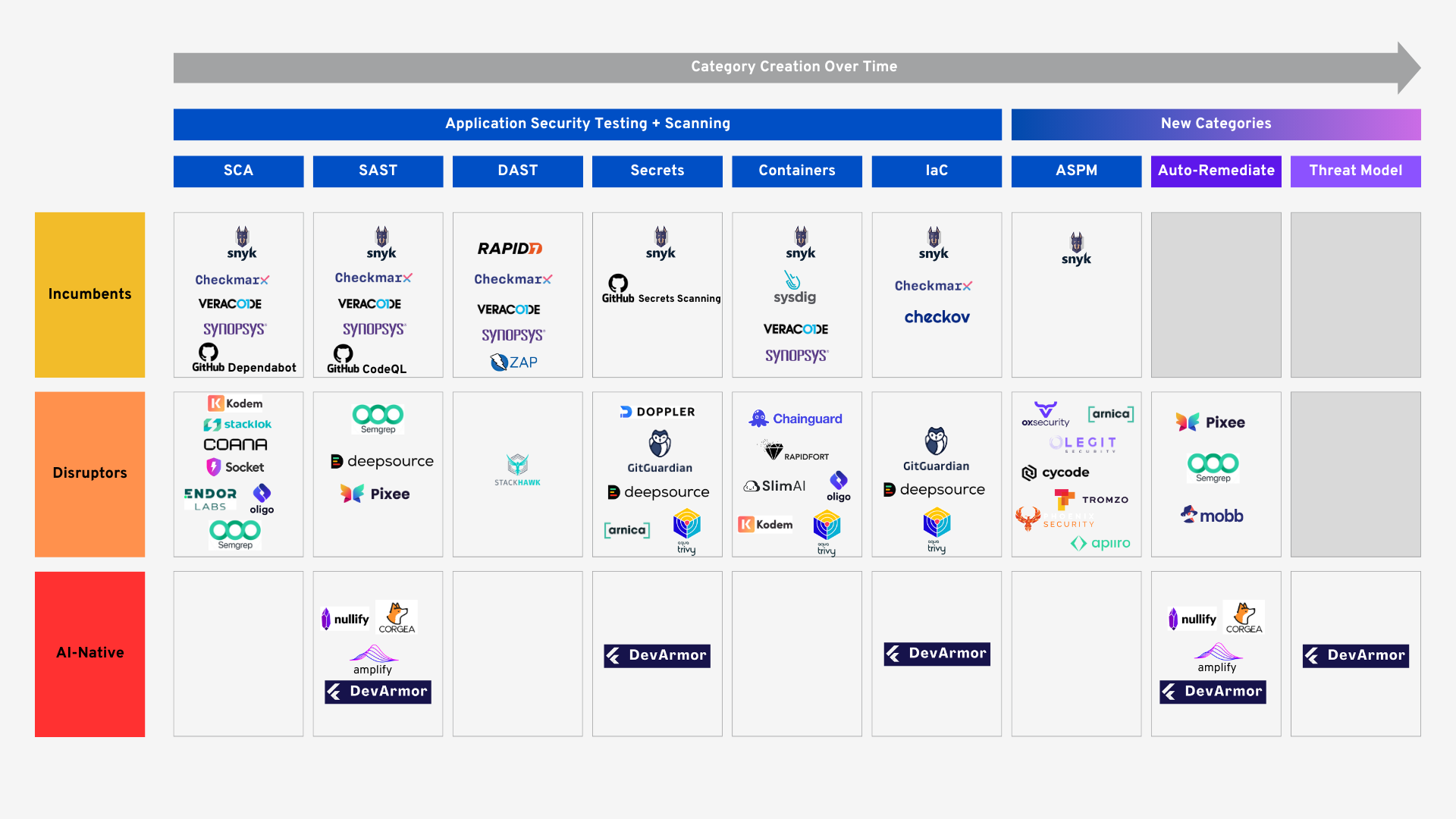
Secure software starts with threat modeling, not scanning. Threat modeling doesn’t replace scanners, it makes them more effective. Scanners identify what’s broken, while threat models highlight what matters.
A Smarter Cycle:
- Threat modeling defines priorities. It identifies attack paths and design weaknesses that deserve attention.
- Scanning provides coverage. It checks that controls exist and catches residual issues.
- Feedback refines the model. Each new vulnerability informs future design decisions.
- Threat modeling gives early feedback to developers and doubles as a teaching tool, so the same mistakes don’t keep repeating.

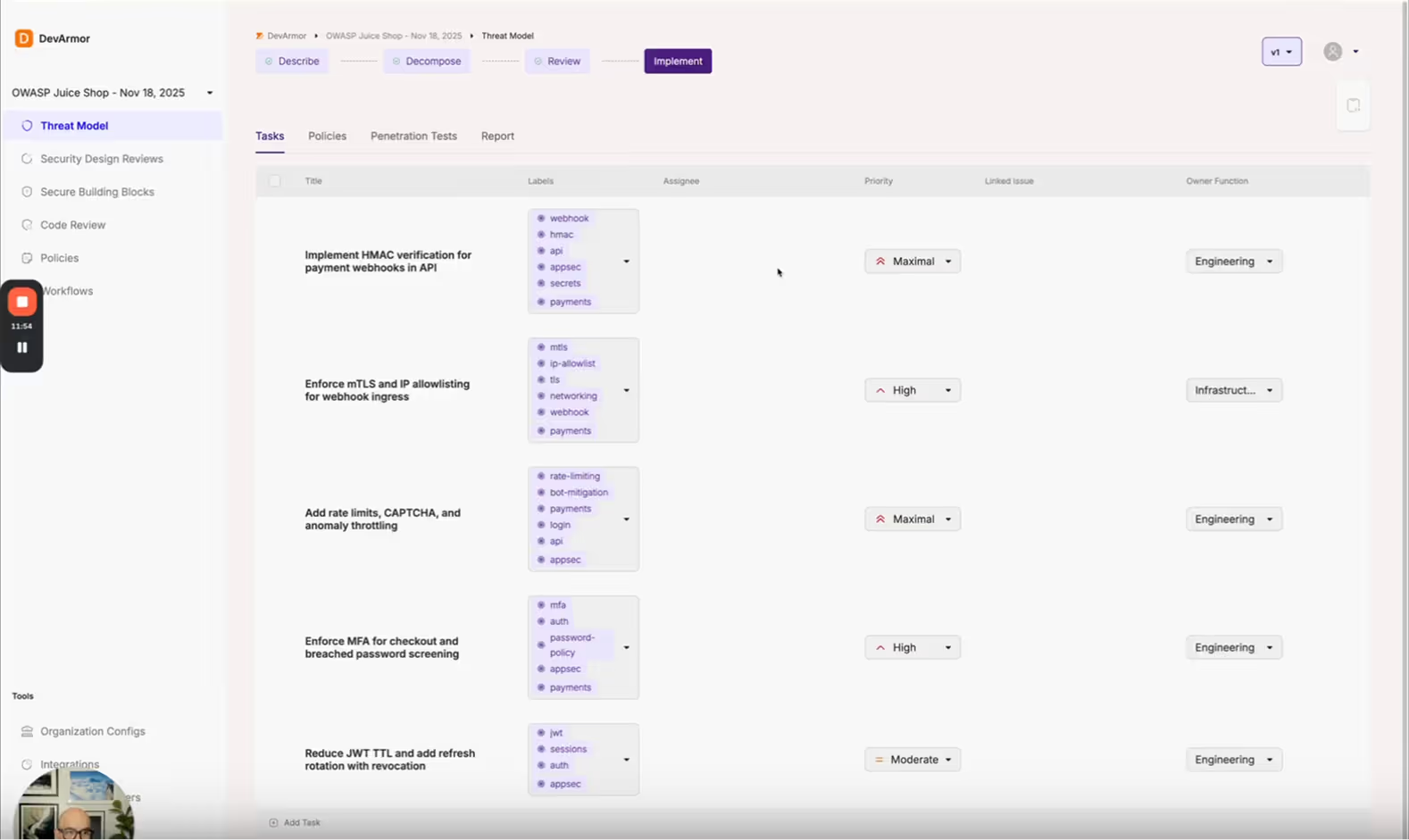
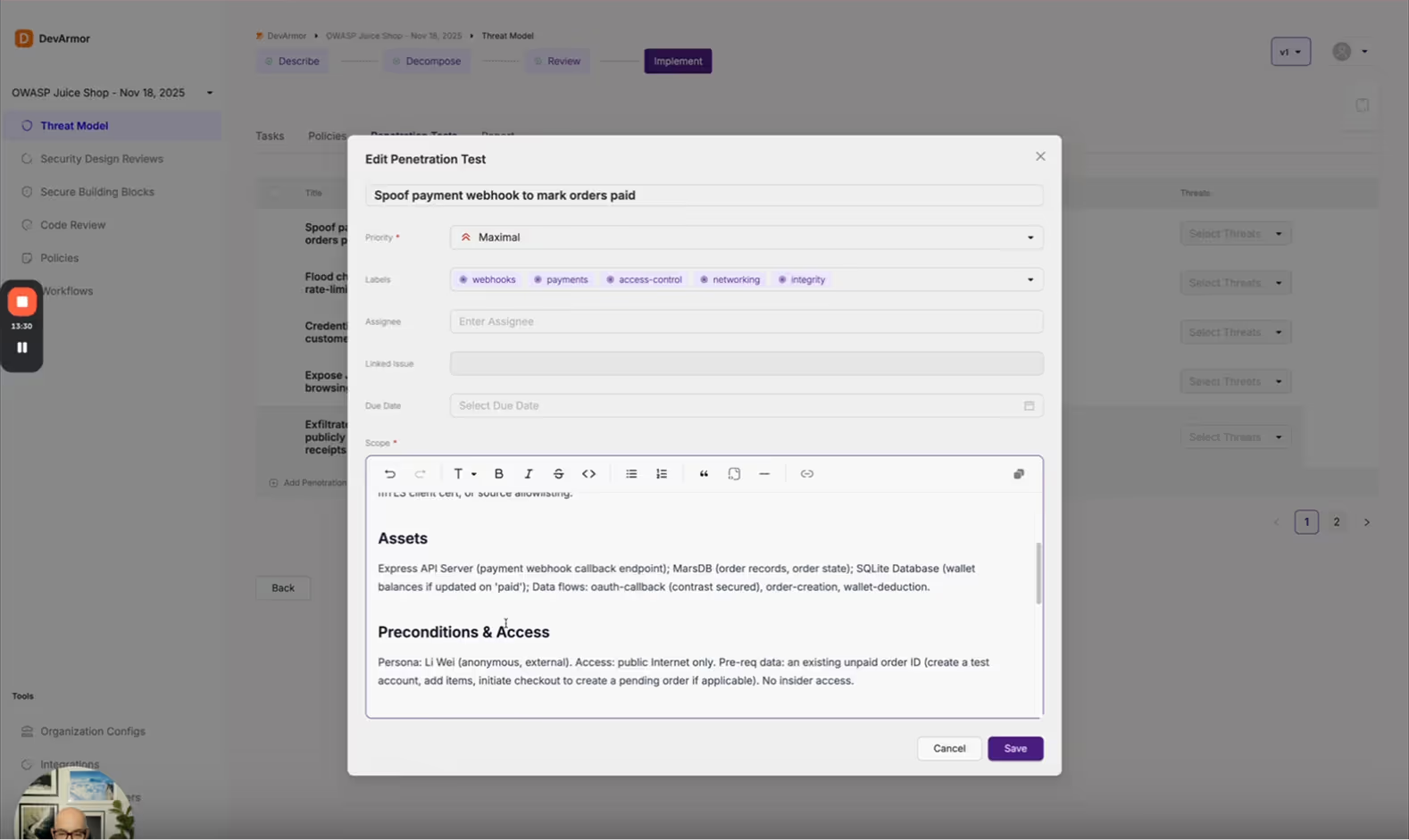
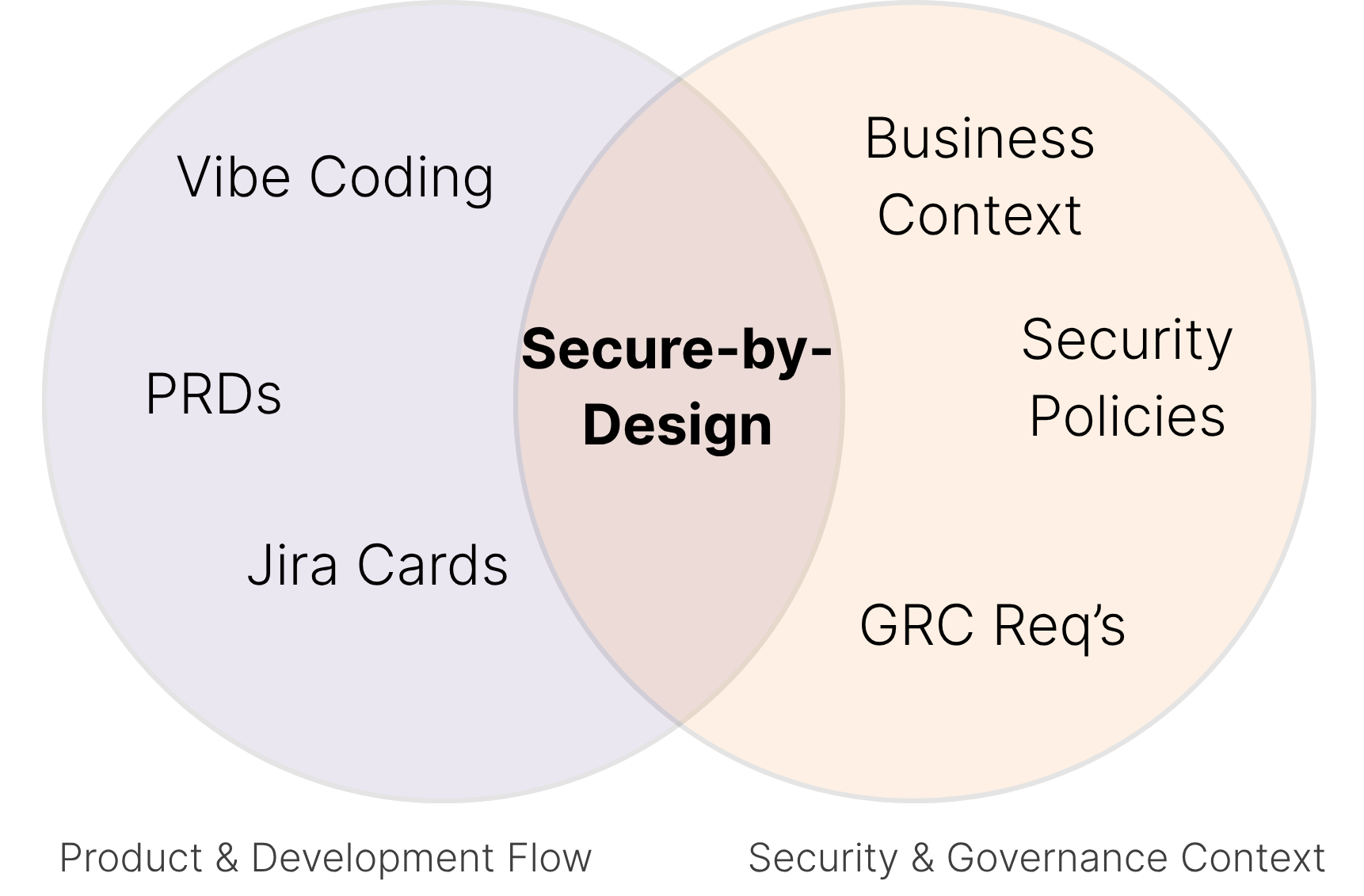
Codify, Automate, and Measure Security Standards
Define your organization’s security standards and map them to real threat models — so developers build securely by default. Run AI-assisted design reviews for every issue and push automated checks straight to pull requests.
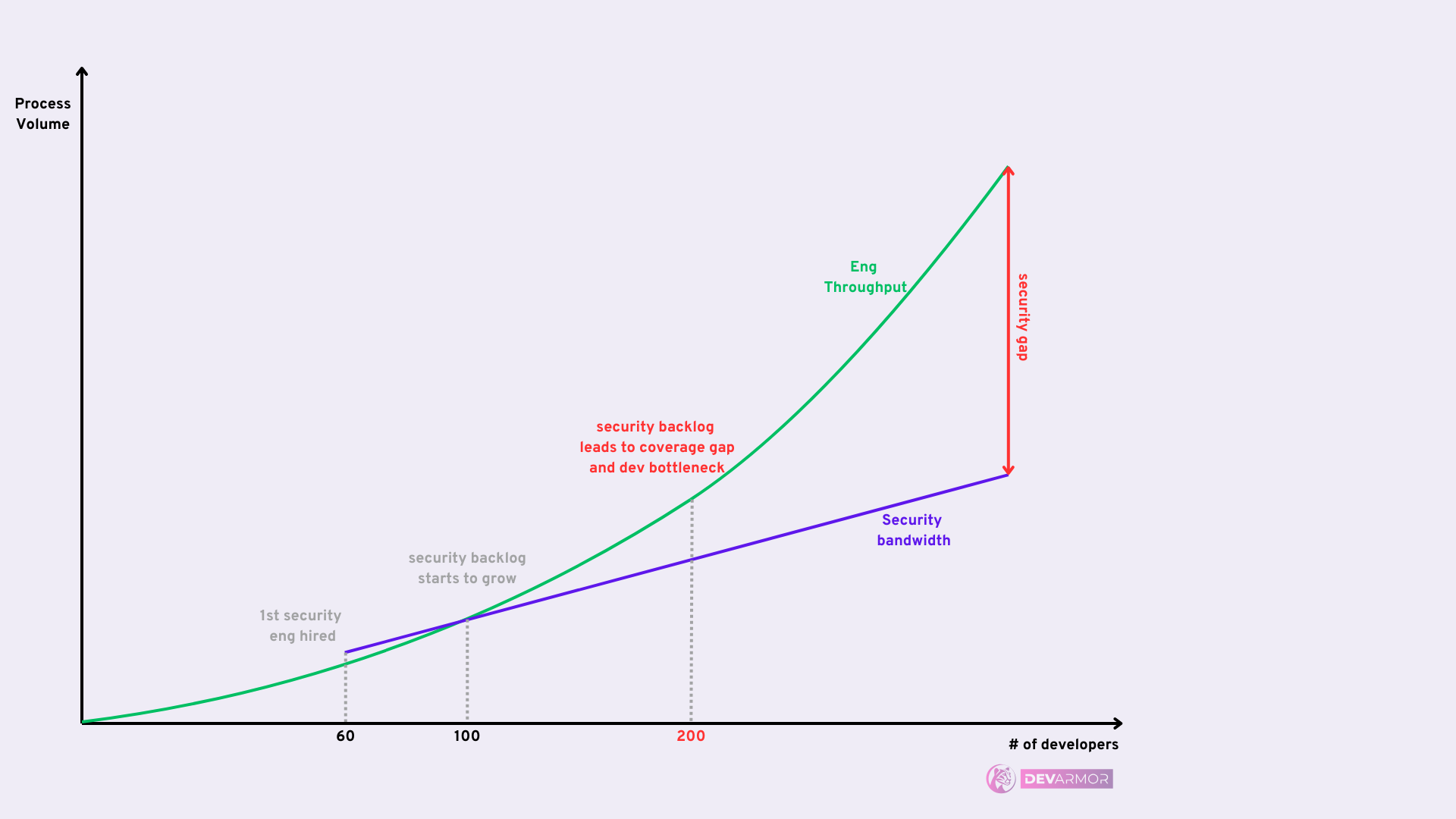
DevArmor provides coverage metrics, drift detection, and per-release attestations, helping security teams focus on edge cases instead of re-explaining the basics